Pros: ??Rapidly and easy account funding ??Innovative tools for traders ??Large stability A small draw back is the fact that rookies may need some time to familiarize them selves With all the interface and System features. Total, copyright is a wonderful choice for traders who price
four. Verify your mobile phone with the six-digit verification code. Decide on Help Authentication following confirming that you've got correctly entered the digits.
Critical: Before starting your verification, make sure you make sure you reside in a very supported condition/region. You can Test which states/areas are supported right here.
Continuing to formalize channels amongst distinctive market actors, governments, and regulation enforcements, while even now protecting the decentralized nature of copyright, would progress a lot quicker incident response and also make improvements to incident preparedness.
Note: In uncommon situations, according to cellular copyright settings, you might need to exit the webpage and check out once more in several hours.
Enter Code although signup to have $a hundred. I absolutely adore the copyright providers. The one difficulty I have had Using the copyright even though is always that check here Every so often After i'm investing any pair it goes so gradual it takes permanently to finish the level after which my boosters I take advantage of to the stages just operate out of your time as it took so very long.
Prior to sending or acquiring copyright for The 1st time, we advocate reviewing our proposed finest procedures With regards to copyright stability.
Facts sharing companies like copyright ISAC and SEAL-ISAC, with associates over the copyright business, do the job to Enhance the velocity and integration of attempts to stem copyright thefts. The industry-extensive response on the copyright heist is a superb illustration of the value of collaboration. Still, the need for at any time quicker motion remains.
Protection commences with knowing how developers obtain and share your facts. Knowledge privacy and stability techniques could vary dependant on your use, area, and age. The developer offered this information and could update it after a while.
These threat actors ended up then able to steal AWS session tokens, the short term keys that assist you to request short term qualifications to your employer?�s AWS account. By hijacking Energetic tokens, the attackers ended up able to bypass MFA controls and obtain use of Safe Wallet ?�s AWS account. By timing their attempts to coincide Together with the developer?�s ordinary function several hours, In addition they remained undetected till the actual heist.
The copyright Application goes outside of your regular buying and selling app, enabling consumers to learn more about blockchain, earn passive income as a result of staking, and expend their copyright.}
 Bradley Pierce Then & Now!
Bradley Pierce Then & Now! Michael J. Fox Then & Now!
Michael J. Fox Then & Now! Matilda Ledger Then & Now!
Matilda Ledger Then & Now!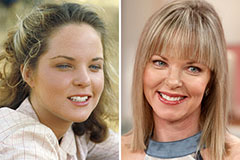 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now! Traci Lords Then & Now!
Traci Lords Then & Now!